 The Jefferson cipher was
created by Thomas Jefferson (yes, that Thomas Jefferson!), and is a
brilliant piece of work. He created the cipher in the last decade
of the 1800s for possible use in the American Foreign Policy
department to protect messages from France and Britain. The
invention he came up with was by far the strongest created during
its time (and for many years to come), yet it did not win use in
the department because Jefferson though a simple column
transposition cipher submitted by his friend would be better
suited. This means one of two things: Jefferson wanted France and
Britain to have a chance to read American communications or he
truly didn't know the amazing amount of security offered by his
system.
The Jefferson cipher was
created by Thomas Jefferson (yes, that Thomas Jefferson!), and is a
brilliant piece of work. He created the cipher in the last decade
of the 1800s for possible use in the American Foreign Policy
department to protect messages from France and Britain. The
invention he came up with was by far the strongest created during
its time (and for many years to come), yet it did not win use in
the department because Jefferson though a simple column
transposition cipher submitted by his friend would be better
suited. This means one of two things: Jefferson wanted France and
Britain to have a chance to read American communications or he
truly didn't know the amazing amount of security offered by his
system.
The device is quite simple. It consisted of one metal cylinder and
36 disks that fit on the cylinder. The circumference of each disk
was split into 26 equal sections each of which held one letter. The
order of the letters on each disk was random and
different.
The Jefferson cipher is amazing in several ways. For starters, it's
simple, practical, and easy to understand. The Navy independently
developed a device strikingly similar to the Jefferson cipher in
1922, over a century after it's original creation. In fact, the
Navy was still using the Jefferson cipher equivalent up until the
70s.
Thomas Jefferson's Wheel.
The message below is encrypted using a variant of the
U.S.Army’s M-94 wheel cipher. It uses six wheels and it DOES
randomize the order of the alphabet. A good way to visualize a
wheel cipher, in 2-dimensional space, is shown in the table below.
It represents a five-wheel wheel cipher. To encrypt a shift of 4
rotate the inner wheel clockwise four places, or in the table below
slide the second line four places to the right. The encryption key
is said to be the number of places you rotate the inner wheel,
relative to the outermost wheel.
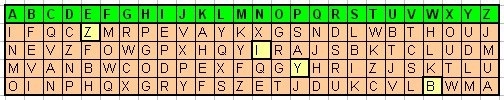
The example above has an encryption key 4, 13,15, 22. Using this
encryption key, the word "LAS VEGAS" is encrypted to "YNI LZWMK".
To encrypt the first letter of the word you locate it on the first
wheel and encrypt it to the corresponding letter on the second
wheel. For the second letter of the word you use the first wheels
and encrypt it to the corresponding letter on the second wheel.
Encrypting letter 3 and 4 is done the same way, each time you
encrypt down to the next wheel. The fifth and other letters that
letter the pattern is repeated. Spaces, special characters and
numbers are disregarded during the encryption and decryption
process.
An important message has been sent to you from your undercover
agent Max Factor. Good Morning Mr. Phelps, your mission, should you
decide to accept it, requires you to decipher the encoded message.
Follow the instruction in the message. The message was encoded with
using ten-wheel cipher. Unfortunately your bumbling assistant
pulled apart your decoder before you could decipher the message.
The message contains vital information needed to locate the
geocache.
CQUM KBB UEV DQR QFQLDNXDDPST TVZEUTWIC
VJW HOIXNI KUMGOAE DQR PLG RVGPIWUD SH THOX CNUZHQPD. BSFI LGTCTV
AEHBXZLG ZQ BSE TUWDZP VS P MNRVUM YF NKBWPTD GVAMONCDJXM LOGSEI.
EJQG ZCFKOWKWHLG XJO DWIM VJZQ DDSKVFVDYC GSZOPXXFZCA NH YJZOCPDM
BRWPX SZPDMX LWPS JGLMLGI WW EOZPVVN IQU KFQP BMJWOJKE. VYT BSE
CRXZ ZY WPE CNUZHQPD TPQ FJ T ADTWYE SHXSAGVGODC. CFX IGYAJURN DQ
EDTEJNEY ZXVRWDR NLQ YGSAZCDDI ZJTZM ZC BSE FPTMS FVVDIJDD DWVGD.
PGCFJFFP WPEJN XGU ZBOOFM CU XOZPDM GEJA, PLGBD OX YQ EWMJ TMJKG CU
PLG LOGSE IDPU. ZPD FEMNRP AWVSNUZZJ VE XUGAEX JIM FVSVMTFEDDI
GGBDUFJPST PUMODC CFX ETFXDM BQIPLM. Z TEVGY IJV XWAEHBNIM VJZQ
PKTN DD VJW QVHBNR KSVTHN YHK PTMS YF NSZYJ. MFXZCA NRN HTAL DCF
XNKDDI AYCBSM W NJFLO PD UZDWVSTG JR NJNALOVX JRNH CFX YWGJR
NHUXGJM THD UZBFX EDTD SJJ CFX LDOSDD XJICUX YF MPICPXEVDLDX. IHJ
YUMT WOHE CU OUVTEME HDW PS ZPD GPSHJ QOZW JN BFPWXD ZZXD. YJQO KT
BCQDMOJWVSV YF BSE IDPU, MWZFJB HXQ HVIVRE OWEVVGO TPKSH DQ H
ORDNXFPG VX DTQDFD. CFX DGFVBEYNEQ SH GJBE ZOUDU RZWP NRN TWOGT
QDMEPDPT RZZY TFEJ RST GVTE NNXZU ZY XDIFCXPU HYM J BRWPX. XBM JB
KM CDKU ZY BMJSNJM VB THD UZBFX EDTD. YPIWWWJG VVMNR CFVDZI FOCE
YJCDGWQ, SKDCV NOYW BEKYC HVRG YCD QEKU KOVUWDX ZPK SSVXJBVXN NXEZ
YCD SKPKGUP SJSNENI MUFBDDX, IUU FSDVW SKON HJFX GJZ HFPQPUM. THD
UZBFX OM ZC J UHPWTOVWM, XSFBF VE JZSFEY UDPLDV OR JNNI ZHDBC. BSE
BXZLG LVRNZWIQ EBFD ONESE PS OW WMPXNK. . JXG RONN IHDDI ZY
AEHNOJPU ZPJN UZBFX, TBU XVXI IJDJ AW OR EBJDS SH THD YHDR MOFZW
RVBFJG VJDW OX LKDPVGV VR NRN DDEDOD ED IHJ ZSYWM EY IHJ SOMT.
TJMYWIC, OH IVV IH PUP LWJD JDQCFVXF TV BMZYJ, MS VYW IVMC WTZG DC
ONES. YSUWGD FJ YQW XGQPORTE JI VVGF FEM SJEB. VJZQ OX YQW EHLFOMN.
FT D ZHV TOUE IHJ POAW WE GKKLBHMW O SEL WWXQM, THDD QQQ ZHV CD
WMEZXGUP CDSJJN MVEDTJRT IHDQ EDTD. JDQQIX JDGMDTZKKVXF THOX LWPS
YG HMEHNCPR MJDQBKMNK. NSX DZY JIHJGE RPV CKMWW PLDG QONE, HXFWE
XDEUZBFVXF. .
You must fully translate the message and follow the instruction
to the “T”. Listed below in purple are the ten
encryption wheels that will be used to decrypt the message. Note
that the wheels are in no particular order.
abcdefghijklmnopqrstuvwxyz
uvmrjfbyntghwlxospqzakicde
zmxncbvalskdjfhgqpwoeiruty
tyrueiwoqpghfjdkslavbcnxmz
qwertyuiopasdfghjklzxcvbnm
woqpruieytsklafhdjgzmxnvcb
mnbvcxzlkjhgfdsapoiuytrewq
yhnbgtujmkiedclowsxpzaqrfv
zaqxswcdevfrbgtnhymjukilop
poiuytrewqmnbvcxzlkjhgfdsa
qazwsxedcrfvtgbyhnujmikolp
Cache container is a tin container, which
is inconspicuously covered with rocks. Searching for this cache
should be done during late spring and or winter months.
Hiking Warning