The principle of using Stegonography to hide a Geocache's coordinates using hidden methodologies in plain files
Authors: Eclectic Penguin, Petra Puffin
Abstract: It is the intention of this paper's authors to hide a Geocache and provide its coordinates using a method called Steganography. The aim is to explain the technology behind this principle and outline in great detail, how the coordinates were encoded and hidden using this methodology. It is hoped that, with sufficient understanding of the principles involved, the reader will be able to find the geocache, using any solutions they can think of, be they conventional or thinking out of the box, through the information conveyed in this paper.
1. Introduction
The coordinates of this cache are hidden in the audio clip you can listen to and download by clicking on the green arrow below (or on the text beneath the arrow).
 Beethoven, Moonlight Sonata, Third Movement
Beethoven, Moonlight Sonata, Third Movement
1.1 Technique
The file containing the Geeocache's coordinates is hidden using a technique called steganography [a]. This is a coverall term which describes the practice of concealing messages or information within other non-secret text or data. The method used here, while using a very simple and well documented concealment method, it is almost impossible to hear or detect, making it a very cunning way of hiding a large amount of information covertly in an otherwise innocent audio clip.
There is an important difference between this method of hiding information compared to cryptography[ b ]. With cryptography, the payload message is hidden in what is clearly obviously a coded message (or something that could be interpreted as pseudo random noise). You need to know the method used to hide the message and often also a key to unlock the cypher.
Steganography however uses what initially appears to be an innocent file such as an image or audio file to imperceptibly embed a message, and this is what we're dealing with here. Of course, if the intention was to hide the message from prying eyes who are expecting to find something hidden, the message could also have encrypted the message that's stegonagraphically embedded - but that's not the case here. Our message is "in the clear" - once extracted, you'll have a file on your PC on which you will be able to clearly read a message and coordinates.
2. Underlying Principles
Before going into the method used to hide the message, here is a brief to explain how pulse code modulated audio coding works, such as that employed in uncompressed audio on CDs and WAV files.
2.1 Analog audio
A sound wave is the pattern of disturbance caused by the movement of energy travelling through a medium (such as air, water, or any other liquid, gas or solid matter) as it propagates away from the source of the sound. In order to make a recording of this sound form, that wave form is replicated electronically and can then be stored on some form of media. In analogue format this wave form can be re-created on some form of media such as waves on grooves [c] on the surface of a record or the varying strength of a magnetic field on magnetically coated tape.
2.2 Digital Encoding
Digitally, the sound wave is recorded using many samples over a known time period, with the level of the wave's amplitude being given a number. The bigger the range of numbers available, the more accurate and better quality the sound. Also, the number of times per second the wave value is sampled is important too - the higher the sample rate, the higher the fidelity.
2.3 The Compact Disc era
When the Compact Disc format was being developed, it was deemed the sample rate of 44.1 KHz (44100 samples a second) was acceptable to record audio to a level that most people would not be able to discern the difference from real life and at the same time fit a standard album on a single side of a disk of the size of a CD using the duplication technology that was available at the time. [d]. Also, it was decided that each sample could be recorded using 16 binary bits giving each sample a numeric value range of −32,768 to +32,767 with 0 being the flat point of the wave. These numeric values would then be converted back to sound using a digital to analogue converter (DAC) and then played back via an amplifier and loud speaker.

In the above diagram, the green line represents the recorded sound wave. Vertically, the value of each individual sample and each bar in the graph represents a sample, with there being 44,100 bars in a second.
This is the sample rate and bit depth used in this example.
3. The Problem Explained
So... where's the message? Many have listened to this bit of classical music[e] and can't hear anything out of the ordinary. Others have analysed it using various digital audio tools on their computers and spotted nothing. Some have even ran it through tools designed to spot and decode common Geocaching puzzles... and... Nothing! That's the beauty of this hide - unless you know its there and know how to extract - it's almost impossible to detect in the first place. Spies use this technique in many forms - so consider yourself a spy catcher if you venture on a quest to find this cache!
So.... how is it done?
The method employed is called Least Significant Bit (LSB) encoding[f]. As mentioned earlier, the audio is encoded using 16 binary bits (known as a 'word'). In binary, it is common to assign each bit a position number, ranging from zero to N-1, where N is the number of bits in the binary representation used. Normally, this is simply the exponent for the corresponding bit weight in base-2. The significance of each binary digit in the sequence doubles in the overall value being explained. The least significant bit (bit zero) of the 16 bit number alters the overall sampled value by only 1 digit...
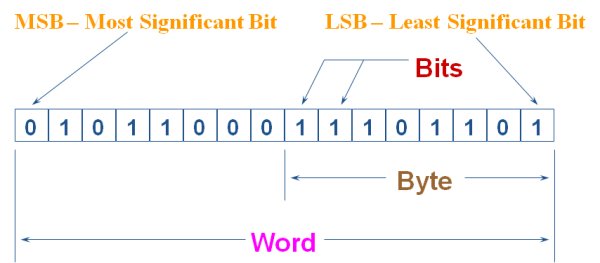
In audio encoded at this level, it would be barely, if not completely imperceptible to the human ear and even to the most discerning ear after amplification, would possibly sound like very quiet hiss, should the LSB be hijacked and used for another purpose all together other than the sound!
And this is what has been done here. For each 16 bit sample in this audio file, the least significant bit has nothing to do with the tinkling of the ivory keys you can hear. Sample by sample, a large and complex message payload has been encoded, one binary bit of the message, per sample. You'll need to skip over the WAV file's header - no message can be encoded here without hopelessly destroying it as a WAV file and this is essential for any player to be able to decode the audio.
The size of the audio file is significant as it contains the entire message payload just once and every single word of audio data is needed. Consider file size - you have 44,100 samples per second - that allows approximately 5.5 kilobytes of message payload per second. If this was a MONO recording - but it isn't so halve that to about 2.8 kilobytes per second...
And yes, "But this is a stereo recording" the astute reader may be asking, having just read that last paragraph "do I decode the left or the right channel?"; The answer here is Either! The same message is embedded in both channels leading to 100% redundancy - a more clever hide could halve the size of the data encoded by embedding half the message on the left channel and the other half in the right. As it is, the data extracted from the left channel could potentially be compared with that of the right channel and if not identical, the assumption could be made that there is an error in the extraction algorithm.
The message starts at the very first sample and ends on the very last sample (hence the abrupt end). There are no message headers, no auxiliary information - just the raw message. As a matter of clarification, This is NOT a straight forward text file you'll be extracting, however the first few 8 bit bytes (characters) of data contain all the information you will need to describe the nature of the file and what to do/name it to make sense on any modern (or ancient) computer.
4. Conclusion
The solving of the problem has been left as an exercise for the reader (of course).
This is difficulty 5 cache because, although the full mechanism that's been used to hide the message has been explained in full, it is believed it will still need a relatively high level of technical skill to extract the message. While there are programs and apps out there that encode/decode exactly the same sort of message, none of these will work with this "out of the box" as they also encode additional information about the hidden message into the audio along with the raw message and unless modified will make no head or tail of this raw encode.
Alert: You are about to download a file that contains further details needed to find this geocache. As the cache owner, I represent that this file is safe to download although it has not been checked by Groundspeak or by the reviewer for possible malicious content. Download this file at your own risk.
5. References

... and further down there's the Solution Checker. If you need to use the checker, our guess is you haven't solved it yet as several have solved it already and haven't bothered. Trust the Penguin....when you solve this puzzle you'll know you have the correct coordinates, so won't need to bother with the solution checker, further below!
The original target area is temporarily(?) inaccessible, for some lots of brainpower has already been put into solving this puzzle - which I don't want to waste. Until the image is re-coded (and this note deleted), a small offset needs to be applied when near the target, S 00.022' E 00.014'. Tweezers may be needed to retrieve the new cache and/or log.